Welcome to Okteto!
Build modern development experiences with Okteto
Okteto transforms the way developers code, test, and deploy applications by offering a seamless, cloud-native development experience. Say goodbye to the complexities of setting up local environments and the discrepancies between development and production. With Okteto, you get ephemeral cloud-based environments, instant code sync, remote debugging, and built-in automations all designed to improve developer productivity and platform team efficiency.
Why Platform Teams choose Okteto?
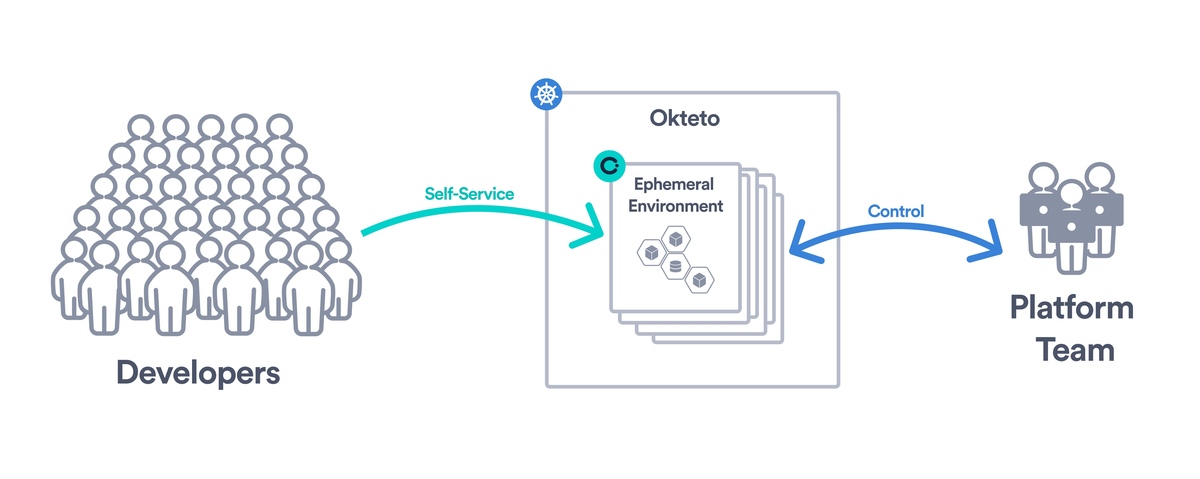
Control, Governance, and Self-service access
Enable your developers to easily access secure and reproducible ephemeral environments. Okteto abstracts the complexity of Kubernetes, providing developers with a straightforward path from code to deployment, all within the cloud. This means no more wrestling with local setup or inconsistencies between environments.
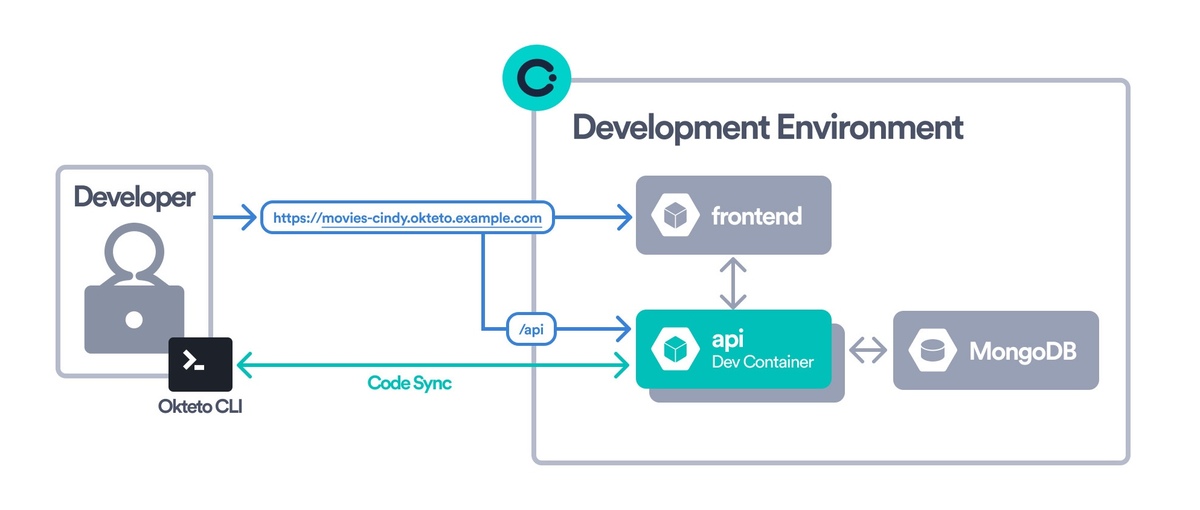
Create a seamless development experience
With Okteto, your development environment is a one-click experience for everyone on the team. Featuring instantaneous Code Sync and Live Updates, experience the magic of seeing your code changes reflected instantly in your cloud environment. This allows for rapid testing and iteration without the need for rebuilds or redeployments, ensuring that your applications run just as smoothly in development as they do in production.
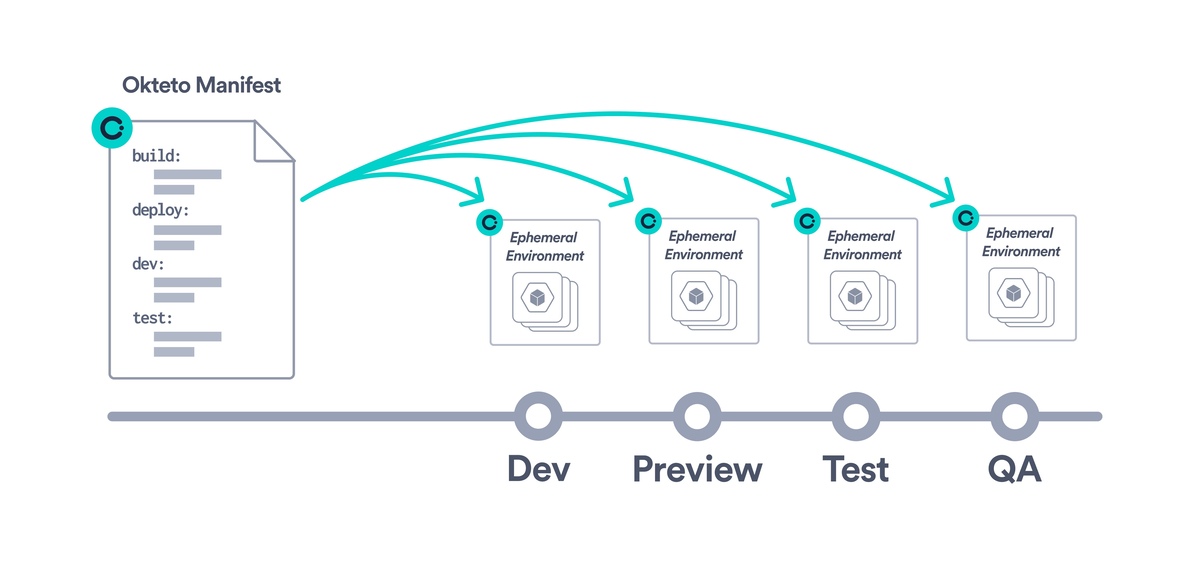
Okteto Manifest simplifies environment automation
Utilize the Okteto Manifest to define and configure your development environments declaratively. This powerful feature ensures consistent and reproducible environments across your team, tailored to your projects' needs. Use the Okteto Catalog to create a collection of ready-to-use development environments for your development team.
Key features
Development Environments
Okteto's Development Environments enable you to deploy and develop applications directly in the cloud with a single CLI command or click of a button. Write code locally on your machine and view your changes live, deployed in the cloud as soon as you hit save! You don't have to spend time configuring anything to do this.
Okteto Test: Shift Left, Test Fast
Speed up your feedback loops by running unit, integration, and end-to-end tests inside your dev environments. With Okteto Test, you can catch bugs before they hit CI without waiting for long pipeline runs.
Automated Preview Environments
Collaborate and share your progress with ease. Okteto's Preview Environments automatically generate a unique, shareable version of your application for each pull request, making code reviews, automated end-to-end testing, and stakeholder feedback a breeze.
Unified management interface
Manage your team's development environments, applications, workflows, and roles all from Okteto's Admin Dashboard. This central hub provides visibility and control over your team's cloud-native development processes, making management straightforward and efficient.
Automated Cleanup and Cost Optimization
Okteto helps you reduce cloud costs without manual effort. The Garbage Collector scales down idle environments and removes unused resources automatically. The Resource Manager adjusts CPU and memory limits based on real usage to avoid overprovisioning. Together, they keep your environments efficient and cost-effective.
Choose How You Deploy Okteto
Okteto is flexible enough to meet your deployment and compliance needs.
-
Bring Your Own Cloud (BYOC): We maintain Okteto, you bring the cloud. You get full control of data and workloads, with none of the management overhead
Learn about BYOC -
Self-Hosted: Install Okteto in your own Kubernetes cluster. Ideal for air-gapped, highly regulated, on-premise environments, or for small teams with Kubernetes expertise
Install Okteto Self-Hosted
Get Started Today
Need help deciding which deployment model or feature fits best? Contact us and we’ll walk you through it.